In symmetric encryption, it is necessary to secure the secret distribution of the keys to the two communication parties, and the process of exchanging the encrypted data can only begin when the secret key distribution is completed. The distribution of secret keys in symmetric encryption has caused considerable problems in practical use, particularly due to the secure distribution of keys by secret channels, which represented weak spots in the concept of symmetric encryption and in terms of communication readiness.
A new approach to key distribution was provided by the Diffie-Hellman algorithm, which enabled the exchange of secret keys via public transmission channel. Later on, this algorithm represented the beginning of cryptography with public key, but it still required a sequence of interactive steps between the participants. The great advantage of public key cryptography is that it does not require any interaction between the participants before exchanging the encrypted text or data. Each participant in a cryptographic system with a public key has two keys - one private key and one public key. The private key is hidden and the public key can be published. Using two keys affects the security level, how keys are distributed, and user authentication. Public key cryptography is universal and allows you to realize basic features such as conceal message content and perform user authentication, or data authentication.
Public key cryptography includes 6 components:
- plaintext
- encryption algorithm
- private key
- public key
- ciphertext
- decryption algorithm
a)
b)
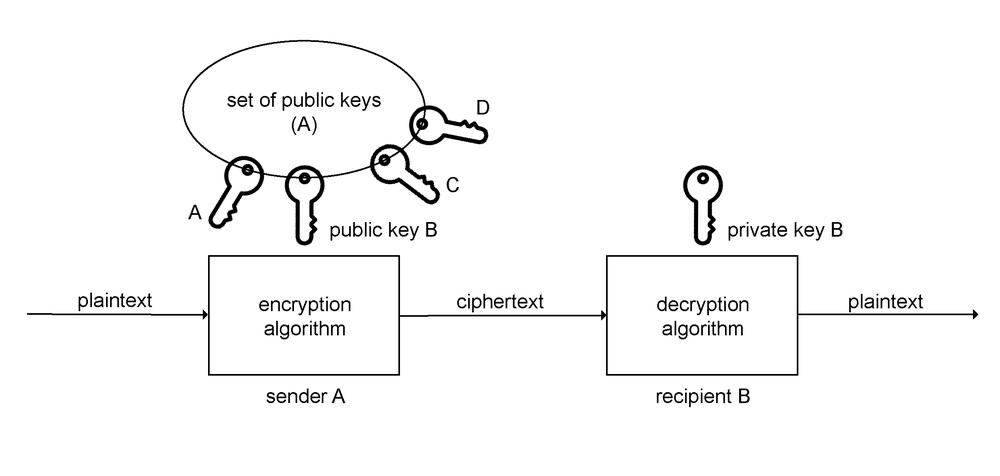
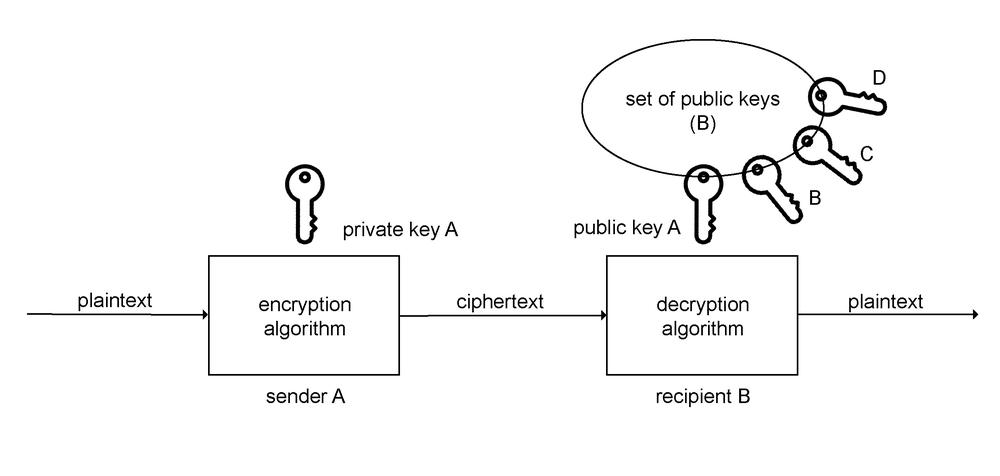
Pic. 0.1 Public Key Cryptography, a) encryption, b) authentication
Public key cryptography provides both, encryption and authentication features. Both features are based on the fact that each communications participant owns their private key and public key. The two keys create a pair. The private key is concealed by every participant and the public key is available to each participant.
Encryption in public key cryptography is implemented with the public key of the recipient. If, for example, sender A wants to send the encrypted message (text) to recipient B, s/he uses the public key B to encrypt. The decryption is performed by private key B, which is owned only by the recipient B.
Authentication in public key cryptography is performed inversely. If the plaintext is encrypted by sender A with their private key, decryption can only be done with the public key A, which means that the message has been encrypted by participant A.
It should be noted that authentication does not ensure confidentiality, i.e. encryption of transmitted messages. There are many algorithms of public key cryptography that have enabled the encrypted messages to communicate, for example e-mail with a large number of users. This enabled mass use of cryptography.
Security of Authentication and Person Identification
An essential area of cryptography for the area of authentication and person identification is the electronic identification card (eID), which replaces the existing identity cards. We are talking about the application of public key cryptography.
It is an electronic version of a personal ID with an electronic contact chip with the following features:
- visual identification of persons - the holder of an electronic identification card is visually identified with the image present on the physical eID.
- digital data form in eID - a specific form of data that includes a digital photo of the card holder and an eID identification file that contains personal data (mainly name, country, date of birth) and other data related to the eID holder. It also contains a hash code of the cardholder's photo and specific data regarding the card number and expiration dates, and which authority issued the electronic ID card.
- authentication of eID holders is the process of their authentication and verification electronically and in real time, i.e. verification of the eID holder
An electronic identification card also enables the creation of an electronic signature in the digital form of a guaranteed electronic signature.
Cryptographic Security in eID
Basic security requirements for electronic identification cards are mainly based on data authentication, the ability to provide data authentication services, and the ability to provide data protection services against data denial.
Cryptographic security in eID is based mainly on:
- the use of cryptography with public key
- the use of necessary digital signature procedures and means in eID
- the creation of publicly known cryptographic security procedures in eID
However, electronic identification cards do not allow prioritizing the encryption and decryption of eID data.
Identification Card
An electronic identification card (eID) with an electronic contact chip can also create a citizen's ID card. For example, eID is issued in Slovakia since 2013. Identification data, certificates for qualified electronic signature (QES), certificates for encryption of eID communication and other data is stored in the eID chip.
The electronic chip extends other possibilities of using the electronic ID card via the Internet and is also a means of creating a secure electronic signature (SES). Currently, the QES electronic signature has been transformed into SES.
Security in eID cards can be achieved in various ways. In particular, it is a personal security code (PSC) which together with the eID card serves to confirm the identity of the eID holder to other natural or legal persons.
The PSC is a combination of six digits that the eID holder chooses when s/he applies for an ID card.
eID Imperfections
Some imperfections were revealed in the eID cards in 2017, the main one being the RSA keys generated by Infineon chips. (RSA is based on the cryptography principle with public key.) The imperfections were revealed by researchers at Masaryk University.
It is possible to get the private key using the generated RSA key. An attacker who would be able to obtain a private key when accessing the eID owner's signature would have the access to the signature of any document without the knowledge of the owner of the eID.
Slovakia and Estonia are among the four countries that use chips from Infineon. In addition to citizens' ID cards, the owners of secure computers with TPM encryption modules, which are used for example for the identification when accessing protected systems, are also affected. The technology is also used in Window's 1.2 version within BitLocker function to encrypt hard disks.
source:
https://www.zive.sk/clanok/128202/slovenske-obcianske-preukazy-vazna-bezpecnostna-chyba/ https://androidportal.zoznam.sk/2017/10/slovaci-pozor-obcianske-preukazy-bezpecnostnu-chybu/
Do you like our articles? Do not miss any of them! You do not have to worry about anything, we will arrange delivery to you.















